There is a stored XSS vulnerability in the ‘ntopng web application’ community edition version 4.1.200612. This vulnerability allows a malicious individual to execute javascript code in the client’s browser in the “datasource” page of ‘ntopng’ web interface.
The vulnerability is found in the “Datasources” functionality in parameter “Name”.
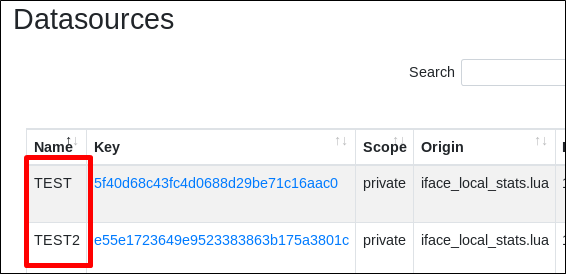
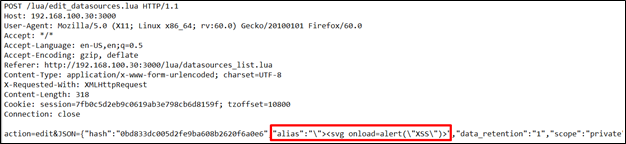
By issuing a POST request while creating a new datasource, it is possible to inject an XSS payload into the name parameter as follows:
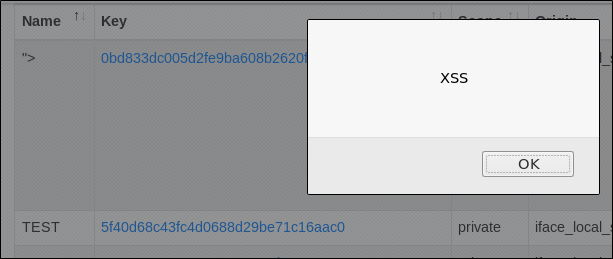
Upon loading the page, the script is executed:
In the “edit_datasources.lua” script; the JSON parameter does not pass any checks before being passed to “datasources_utils.add_source”
It may be possible to load external JavaScript files to execute them and perform advanced attacks.
As this vulnerability requires access to a user account, it doesn’t require an urgent fix, but it may be feasible to fix this in the next release.
By Ihor Voschyk
LL advises to all the researchers do not break real applications illegally. This fun leads to broken businesses and lives, and, most likely, will not make an attacker really rich.